Why Spyware Might Slow the Internet of Things Adoption
The Internet of Things (IoT) is touted as the next frontier in technology. Many are banking on its potential to improve daily life through broader automation and greater connectivity.
While the IoT offers benefits in many areas, it also comes with a few caveats, one of which is the ever-present threat of data breaches, which is a 21st century technical reality. Today's hacker looks to exploit ANY device connected to the Internet.
Scam Detectors Most Trusted Websites in Online Security
- Guard.io (100): Surf the web safely. Clean up your browser, remove maliscious extensions and check for privacy violations.
- Incogni.com (100): Delete your personal data from the internet and protect against scams and identity theft.
- ExpressVPN (100) Stay secure and anonymous online - Best VPN Out There
- IPVansish (100) Fast VPN to stay safe and secure online with multiple discount plans.
With the nature of the IoT to be connected to the Internet 24/7, concerns over its ability to protect users have drawn more attention from cybersecurity experts and the general internet-using public. Consider the following a mini-education on the Internet of Things, the prevalence and different strategies deployed by hackers against it, and a few things you can do to prevent attacks.
What is the Internet of Things?
Watch the video below to see a short, to-the-point explanation of IoT:
The Internet of Things Explained Video
The Internet of Things is defined as devices that are connected to the Internet and other network solutions. Think smart refrigerators, home assistants like Amazon Echo, video doorbells, or home security systems.
Given that they are connected to a network, these simple products are given new capabilities. For example, a light bulb can be controlled remotely or security cameras can be monitored and adjusted via a smartphone even when you are on a business trip far from home.
The term was first introduced in 1999. The Internet of Things is expected to have grown to 20.4 billion IoT devices by 2020. The rapid adoption of this technology probably has a lot to do with the interoperability and convenience these devices bring to our lives.
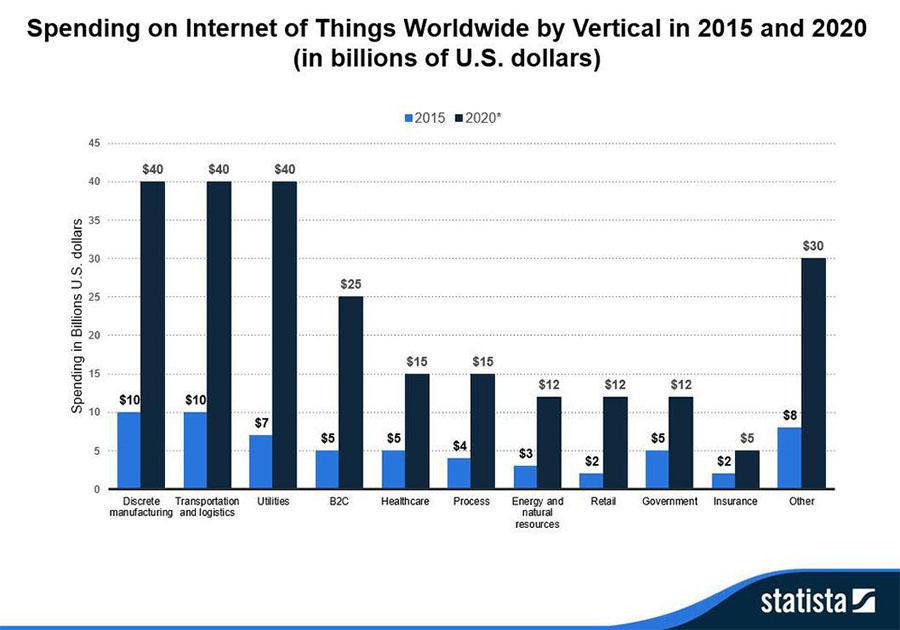
And when it comes to adoption, it seems like we're just getting started. The growth rate is expected to accelerate in the coming years. A Statista report disclosed that manufacturing, transportation and logistics, and utility industries are expected to drive the IoT growth in the coming years, with spending by these industries estimated to hit $40 billion each by 2020.
What About IoT Security?
IoT devices are not spared from the kind of data breaches we read about every day. Hackers interest in these kinds of networks is driven by the extreme lack of security measures protecting them.
Trend Micro, one of the leading security firms in the world, revealed several security concerns. The report noted that most companies embracing this technological advancement are becoming aware that issues like cost and information technology (IT) complexity, higher security complexity, data security, and network security will all have to be considered in the determination of how quickly they adopt the idea.
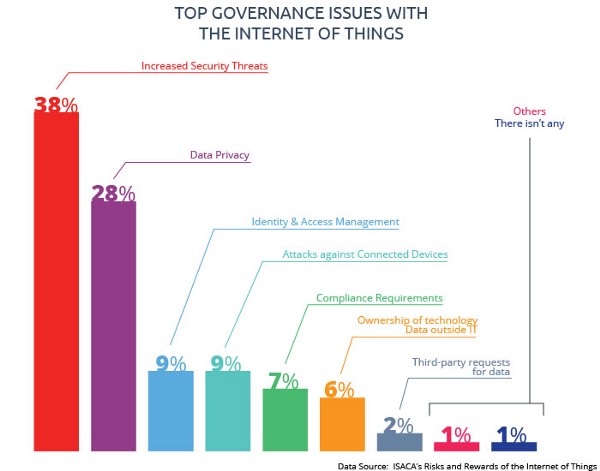
While the world falls in love with the IoT, company IT teams and security experts have to consider the cybersecurity threat differently. Security breaches stemming from hacking Internet of Things devices can lead to the following:
- Decreased customer trust
- Profit loss
- Damage to brand reputation.
Spyware and IoT
Spyware is a type of malware (software) covertly used to transmit data from an individual or organization's network or internet-connected device without their knowledge. Its use in rampant today.
The report “Protecting Consumer Privacy in an Era of Rapid Change,” from the U.S. Federal Trade Commission named spyware as one of the most significant security threats faced by devices operating under the IoT umbrella. Hackers see this as an untapped opportunity for profit.
But hackers aren't the only ones deploying spyware into the IoT. One concerning statement came from James Clapper, U.S. director of national intelligence and a guy that should know a thing or two about the topic. Clapper said before a congressional committee that spyware could be used by the government to identify, conduct surveillance, and track locations.
What Can Be Done?
With the threat of spyware looming over the growth of the IoT, threatening to dampen enthusiasm, there are various ways security experts suggest dealing with the associated security issues.
For consumers and industry alike, a good bit of protection can be found through the installation of a virtual private network (VPN) on the router that handles your IoT devices. This privacy software masks the IP address of any networked IoT devices and also encrypts data when it leaves the network. The overall gain in using VPN technology is that it exponentially decreases the chances of a hacker finding your network on the open internet, and if they do manage to detect your connection, any data intercepted will be unreadable and unusable.
Service providers typically offer plans in the $5-10 range per month, though third-party VPN reviews and security forum threads can help pinpoint free alternatives if you're not excited at the idea of yet another paid subscription. Research carefully if you go the no-cost route because some vendors have shown themselves to play fast and loose with customer data by logging your activity and turning the results over to advertisers or government busybodies.
Protocols and Standardization Initiatives
Cybersecurity experts point to designers and manufacturers of devices intended for IoT use as part of the problem, suggesting there are ways to incorporate greater security in them from the start. The importance of adopting standard communication protocols can't be overstated. Given that these devices are connected to the Internet 24/7, existing security mechanisms generally used online could be redeveloped and applied to the Internet of Things.
Key Layers of IoT
Device manufacturers need to study further, understand, and develop security measures based on the different layers of this new technology. Explicitly, IT executives and cybersecurity professionals must give more attention to the following security layers:
Application layer – This layer covers all various applications and services provided through the IoT. It includes smart cities, smart homes, and automated vehicles.
Perception layer – Sensory technologies mostly comprise this layer. It includes temperature sensors, pressure sensors, vibration detectors, and radio frequency identification (RFID) sensors.
Network layer – This category combines network communication technologies and its physical components that include servers, network nodes, and other devices used for IoT devices to communicate with one another.
Physical layer – Physical layer pertains to primary devices in IoT, which includes smart appliances and power supplies that support intelligent devices.
Possible Solutions
The Internet of Things presents obvious benefits to everyday living by making processes more efficient and smarter. But until we get a handle on the associated cybersecurity threats, full-scale adoption will likely be slowed to some extent, even as it rages out of control – people will eventually grow tired of the constant hacking and presence of malware and spyware.
And even though data breaches are the norm on today's internet, concern over the porous nature of IoT security will hopefully prod device manufacturers and cybersecurity experts alike to find solutions that work. A few possible avenues of exploration include blockchain technology, artificial intelligence, and machine learning, perhaps used in combination with existing tools like firewalls, VPNs, and malware detectors.
Stay tuned. This topic isn't going away any time soon.
Verify a website below
Are you just about to make a purchase online? See if the website is legit with our validator:
vldtr®


TOP 4 MUST-WATCH FRAUD PREVENTION VIDEOS
1. Top 5 Amazon Scams in 2024 2. Top 5 PayPal Scams in 2024 3. How To Spot a Scam Email in 2024
- Latest Posts by Selma Hrynchuk
-
Compromised Credit Card Scam
- -
Fake Google Chrome Update
- -
Facebook Privacy Notice Hoax
- All Posts